Remote Control
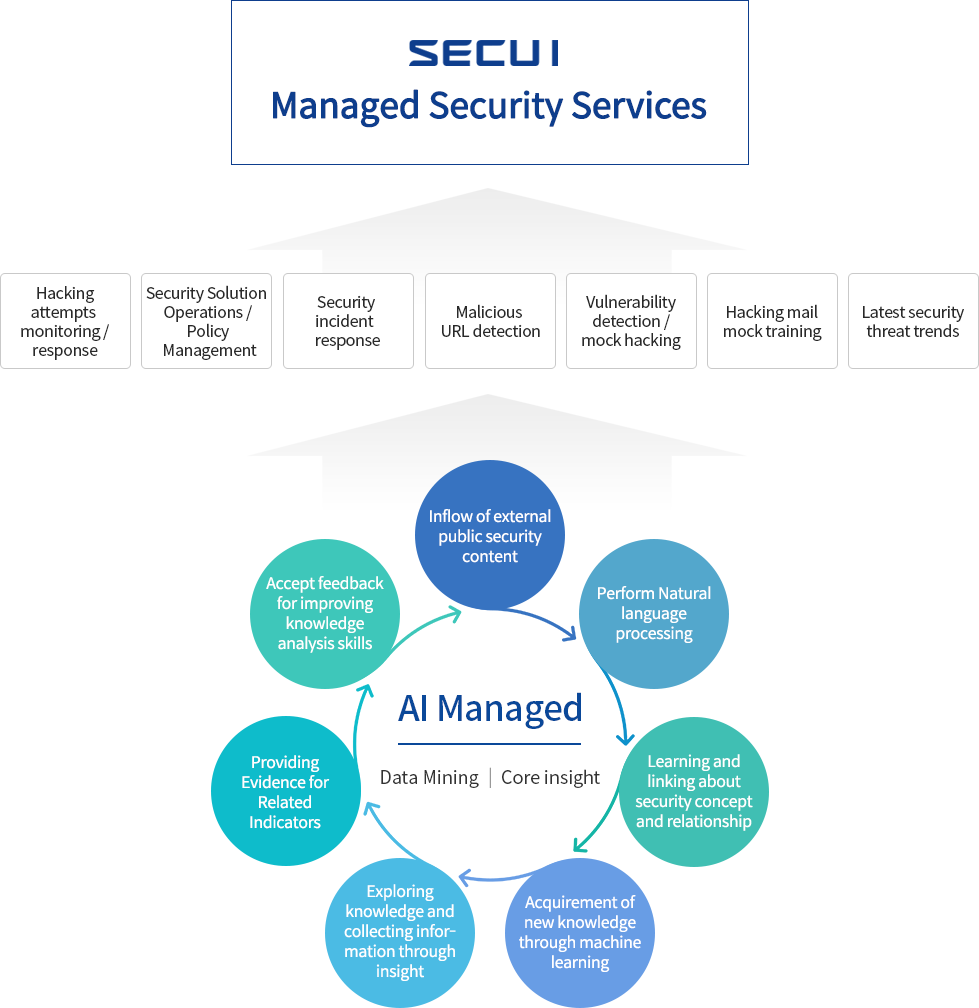
Deep technology of the manufacturer and global best AI-based differentiated Managed Security services
-
AI-based Managed Security services
-
- Cognitive-based AI (artificial intelligence, IBM Watson) analysisto detect potential threats
- Quick Response and flexible Threat Hunting
- Responding to AI-based cyber attacks
-
- Alignment between security analysts and technology elements through the integration of AI technology shortens detection time and improves accuracy of detection
- Advanced Threat Detection
-
- IBM Security Response Preemptive response to the latest and global security threats using IBM X-Force
- Defense of Creative Attacks by Automatic Update of Global Threat Information
-
As the best network security solution vendor in South Korea, In-depth technology-based analysis
-
- Integration of know-how accumulated from technology development and consulting know-how of information security professional service company through development of security solution
- Operate engineer-level control personnel on security solutions
-
- Establishes a Threat Intelligence (TI) organization that collects information on security management operations organization and external threats
-
Global Standard Level
-
- Collaboration services between SECUI's skilled security manpower and IBM's threat analysis expertise
- Applying IBM's top-level analysis process
-
- Provide global analytic services for security Incident emergency response (IBM's 24-hour analytical service)
Major Control Service
Security System Service Type
| Category |
Service |
Optional Services |
FW/IPS
Anti-DDoS/WAF
Anti-APT/Webshell |
Solution Integration Event Monitoring (24 * 365)
- Security system failure / performance monitoring (Alive Check)
- Integrated security event monitoring
- Failure monitoring
Cyber incident response service
- Hot-line support in case of intrusion
- Provide incident response and analysis report
Reporting Services
- Send Monthly Control Service Report / Provide periodic security information
- Ability to view customer reports through the Web
Technical Support (24 hours)
- Security Technical Support
- Service improvements and complaints received
|
Security Solution Operation Service
Security Solution Delivery
- Security Solution Leasing Service
Security Solution Operation Service
- Security Solution Remote Management / Operation
- Security Policy Configuration and Remote Update
|
| Detect malicious URLs |
Detect malware route for domain (URL) operated by customer |
|
| Detect vulnerability |
Analyze target systems
- Analyze information flow and derive expected vulnerability
- Define the target system to check for vulnerabilities
Mock Hacking and Vulnerability Checking
- Hacking the system / service in the same position as the hacker
- Check for data leakage and internal accessibility of malicious code / APT attack type
- Vulnerability Checker and Vulnerability Check
Establish improvement tasks
- Diagnostic report on vulnerability and cause analysis�
- Suggest measures for major causes by diagnosis area
- Quick fix based on priorities / Short-term / long-term improvement tasks
|
Mock penetration test
- Penetration testing of customer's operating system in the same environment as external hacker
|
| Hacking mail mock training |
Simulated training in a pattern similar to actual malicious mail
- Send hacking mail (malicious / spam) to employees with a fictitious account
- If you click on the link and click Attachment
- The hacking mail reader recognizes the infection and reports it
|
|