Security Consulting
Based on the experience and specialty in information security consulting field we provide client oriented service.
- according to what the client wants, we serve from inducing information security solution to efficient information system operation.
- by doing the project together with the clients, we provide know-how of consulting, and let them able to operate by themselves.
- after end of the project, by continual client service, we provide solution and find out problems.
Based on the experience and specialty in information security consulting field we provide client oriented service.
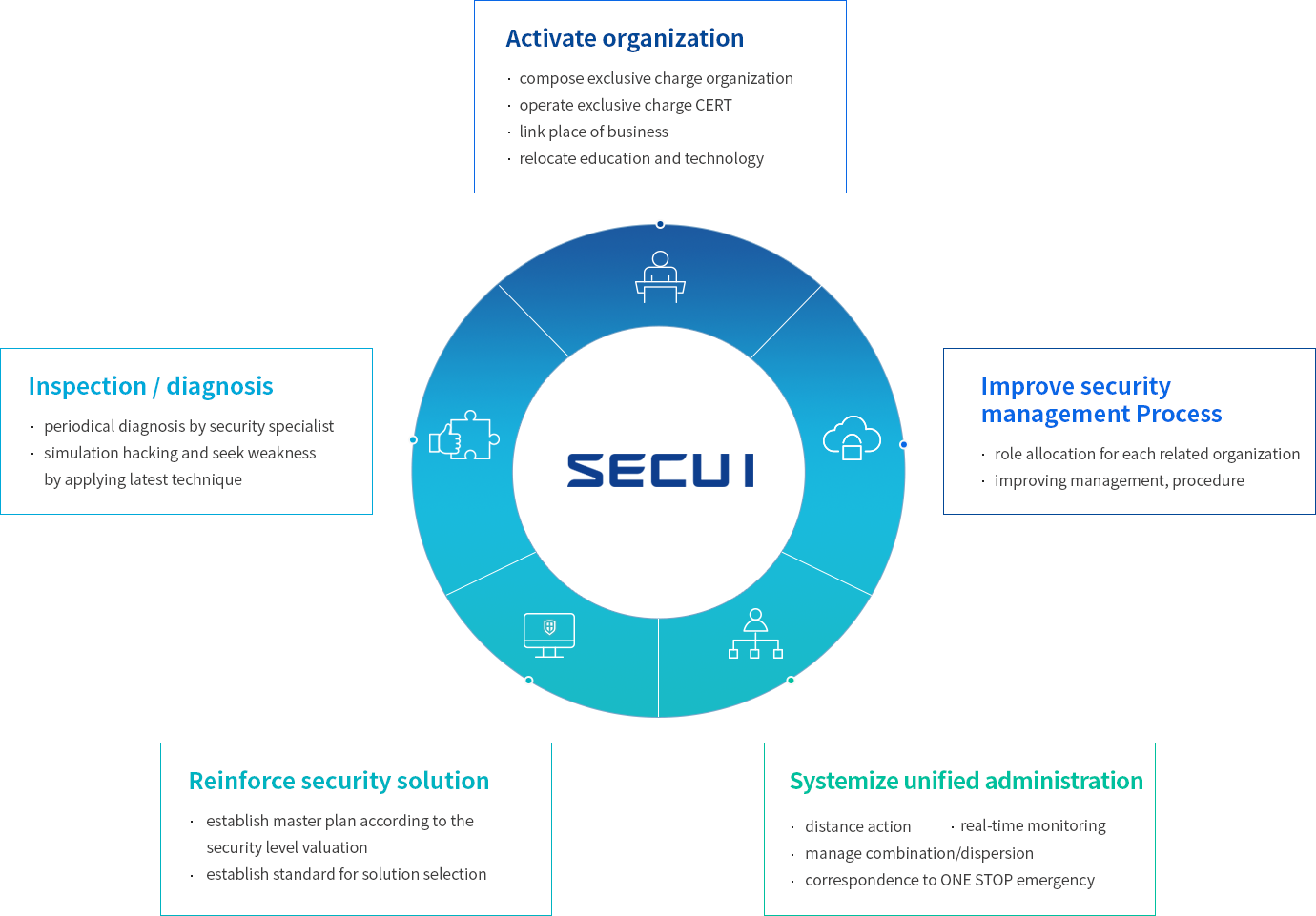
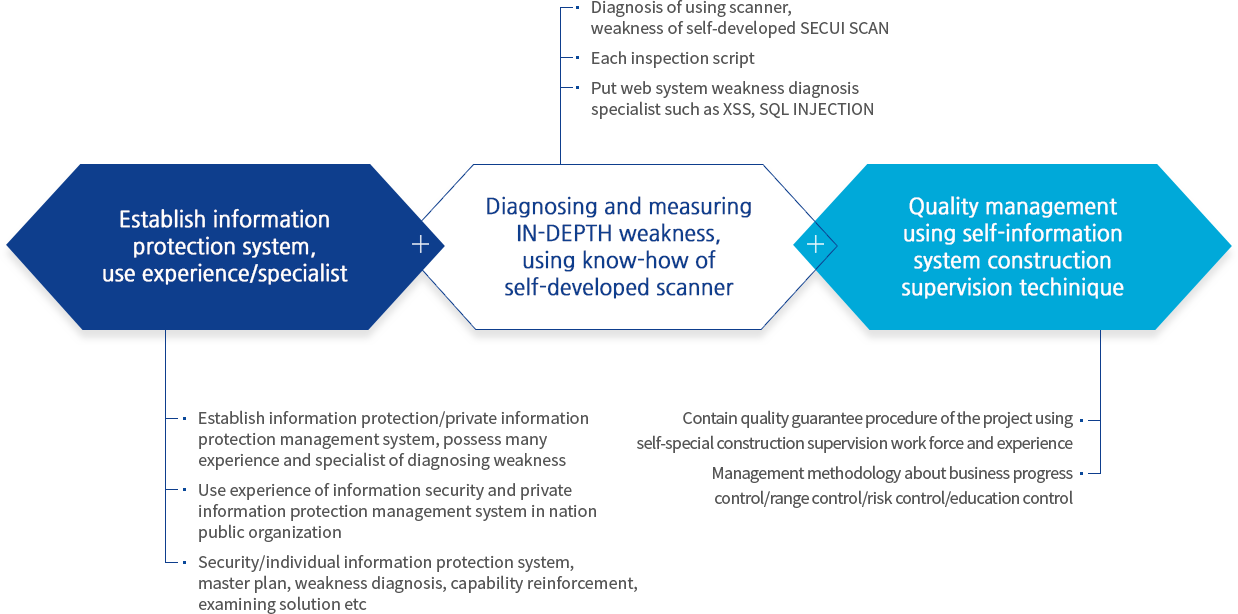
The discrimination of SECUI security consulting is that we have the best specialist who has done variety of projects and use deep weakness diagnosis know-how, and through quality management using information system construction supervision technique, we guarantee successful company work.
SECUI is providing professional and customer-oriented information protection consulting targeting private enterprise and nation main information communication infrastructure.
| Consulting classification |
Features |
Subject of application |
Necessary period |
| Analysis and evaluation of weakness of main information communication and e-banking infrastructure |
Information protection consulting service to establish protection measure and weakness analysis/evaluation about main information communication infrastructure of main information communication and e-banking infrastructure protection |
- main information communication, e-banking infrastructure management facility, jurisdiction central administrative agency
|
3 weeks |
| Provide certification of ISO/IEC27001, KISA-ISMS/PIMS |
Providing certification consulting service to achieve private information protection management system and information protection management system certification |
- company who is wanting to use information protection as a strategy
- company who is trying to adopt standard information protection or private information protection management system
- subject of duty: company who has to achieve ISMS according to 「law related to information network system encouragement of use and information protection」
|
3 months |
| Private information influence evaluation |
Private information integrated security management service that prevents leak/violation of private information and provides follow-up service |
- company that use/collect/save private information in customer service process
- subject of duty: private file and selected processing system operated by public institution according to private information protection act no.2-6(when therer is change or establishing)
|
1 month |
| Diagnosis of simulation hacking/security weakness |
Fulfill technological diagnosis of target system including penetration testing by CERT organization, and provide countermeasure |
- company who is willing to secure technological safety of information system
|
2 weeks |
| Combination security |
Customer-oriented consulting service that perform diagnosis, analysis, plan, master plan targeting managerial, technical, physical security of normal company or organization |
- company/organization who needs information protection master plan through diagnosis and understanding of current situation
|
3 months |
SECUI provides personalized information protection consulting service that is just right for the customer.
| Service classification |
Features |
Subject of application |
Main task |
Necessary period |
| Web application code auditing service |
Service that provides certification follow-up examination or provide base protection facility protection countermeasure through periodic weakness diagnosis in annual maintenance contract program after doing consulting |
- ISO27001/ISMS certified company
- main information communication infrastructure
- need security reinforcement by 3 party
|
- weakness diagnosis
- simulation hacking
- security inspection
- correspond to infringement accident
|
1 year |
| Solution setting and BMT providing service |
Supporting establishing information protection system or conduct BMI targeting company or organization who is trying to impose information protection system of latest technology successfully |
- company who’s trying to impose information protection system of the latest technology
|
- establish solution selecting guideline
- BMT
|
2 weeks + |
| Web application code auditing service |
Providing application code inspection and web application security development guideline targeting company/organization who has high dependence in E-biz |
- company/organization who is trying to check the safety of web application
|
- establish application development guideline
- simulation hacking
- application code
|
2 weeks + |
| Security auditing agent service |
Targeting company who needs security inspection by the 3 party for reinforcement of internal security |
- company/organization who wants third party security inspection
|
- simulation hacking
- security inspection
|
2 weeks + |
| Personalized security diagnosis service |
Providing countermeasure of information security having security claims of normal company or organization as a standard |
- company/organization that demands security service that is right for certain purpose
|
|
2 weeks + |
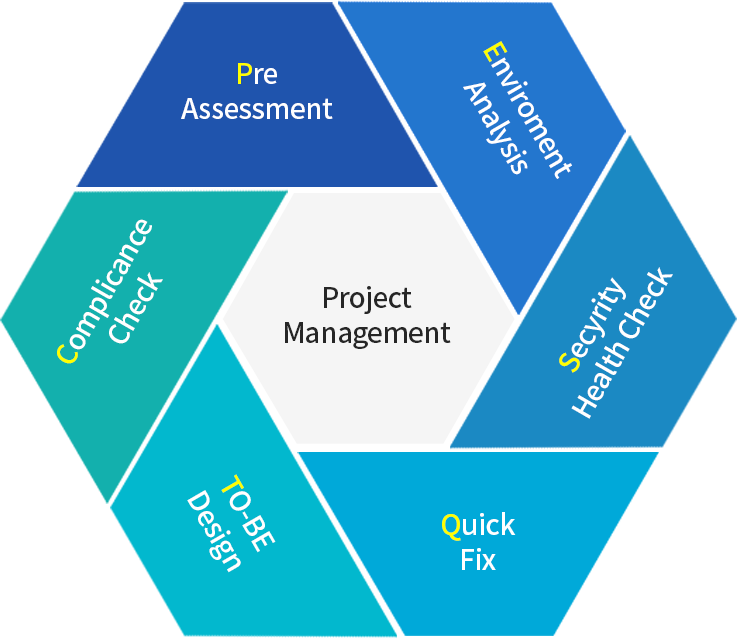
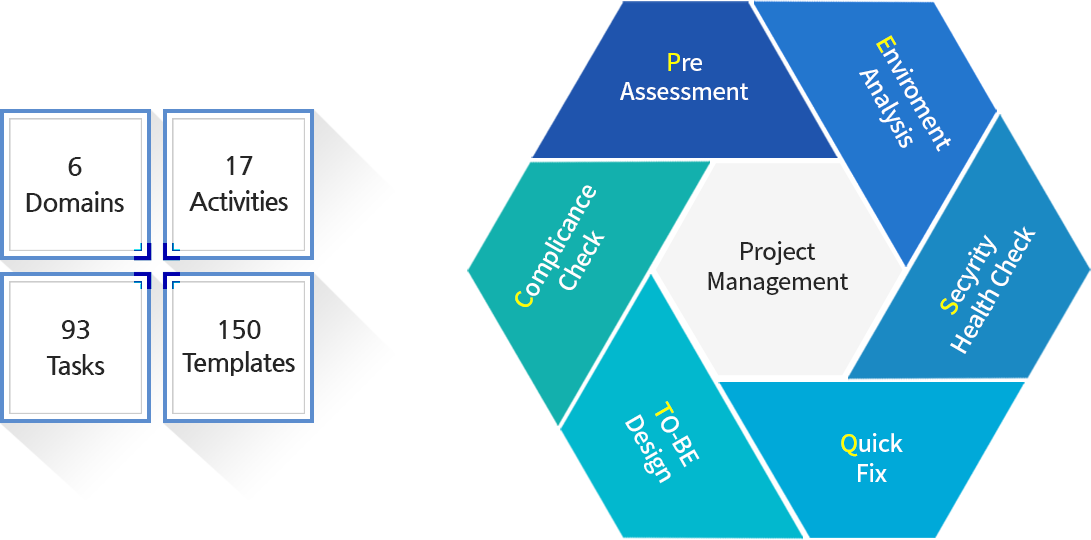
We aim perfect project management with professional analysis through qualified methodology.
-
Pre
Assessment
- Define PJT
- Prior education
-
Enviroment
Analysis
- Environment analysis
- Analyze management system and organization
- Review PJT
-
Secyrity
Health Check
- Set risk analysis range
- Examine and distinguish asset
- Analyze risk element
- Analyze weakness
- Risk examination
-
Quick
Fix
- Hands-on staff education
- Emergency measure
-
TO-BE
Design
- Establish system
- Plan guideline
- Plan technological system
- Master plan
-
Complicance
Check
We can expect not only improvement of security management level, preparation of information protection invest base, but also increase customer credibility and secure legal standard through successful consulting.
-
Internal effect
-
Improve information protection management standard
- Improve security level of implementation through process planning and revision of policy
- Continuous standard improvement and deduct quantitative security level
-
Prepare information protection investor base that is cost efficient
- Grounds deduction of technique security investment through security architecture actualizing
- Use mid to long term information protection investment road map through aster plan establishment
-
Effective management of information protection weakness
- Secure information communication facility security such as network, server, DB
- Deduct security management method for self-develop operating application
-
External effect
GAUSS methodology is a SECUI consulting methodology that systematically organized policy, process method, equipment that is needed for inspection, control, security of information system, that is standardized into six.
Gauss methodology is develop to fit just right for domestic environment through variety of experiences and standard. It guarantee successful project procedure through improvement of productivity and quality through follow-up management, quality review for each stage, optimization according to the customer needs and project characteristic.
-
Combined methodology based on site
-
- Optimize performance based on the analysis of customer business characteristic
- Increase customer capability by maximizing customer participation, systematic education and technology transfer
- Analysis and diagnosis about information protection field and technology element
- Use latest variety analysis and diagnosis technique
- Automatic equipment, simulation hacking
- Security test
-
Continuous improvement and progress
-
- Improvement and using templet, checklist and follow standard process
- Gain and manage variety of project experience and knowledge
- Apply circulation model of each level, plan, progress, check-up, improve
-
Methodology that is verified internally & externally
-
- Accommodate construction supervision standard and internal/external security
- COBIT, ISO27001
- KISA ISMS
- FSS security standard
- Fulfill project successfully by applying it to many public institution and infrastructure
- Apply systematic and consistent project management technique